NSA Codebreaker 2022 Task B2
Description:
It looks like the backend site you discovered has some security features to prevent you from snooping. They must have hidden the login page away somewhere hard to guess.
Analyze the backend site, and find the URL to the login page.
Hint: this group seems a bit sloppy. They might be exposing more than they intend to.
Solution:
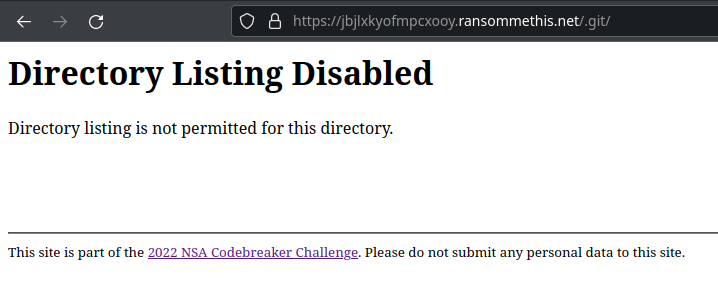
As stated in the challenge description, there is an information leak on the website that reveals the path forward. Analyzing the request headers reveals an unusual request header; x-git-commit-hash. This implies that the web developer was using git for version control and may have left the .git directory at the root of the website. This is shown to be true when querying https://jbjlx<redacted>pcxooy.ransommethis.net/.git/ which returns Directory Listing Disabled instead of a 404 error.
The files inside this .git directory can be recovered by using git-dumper. This tool will not only recover the .git folder, but it will also recover all of the website’s source code.
git-dumper https://jbjlx<redacted>pcxooy.ransommethis.net/.git/ source
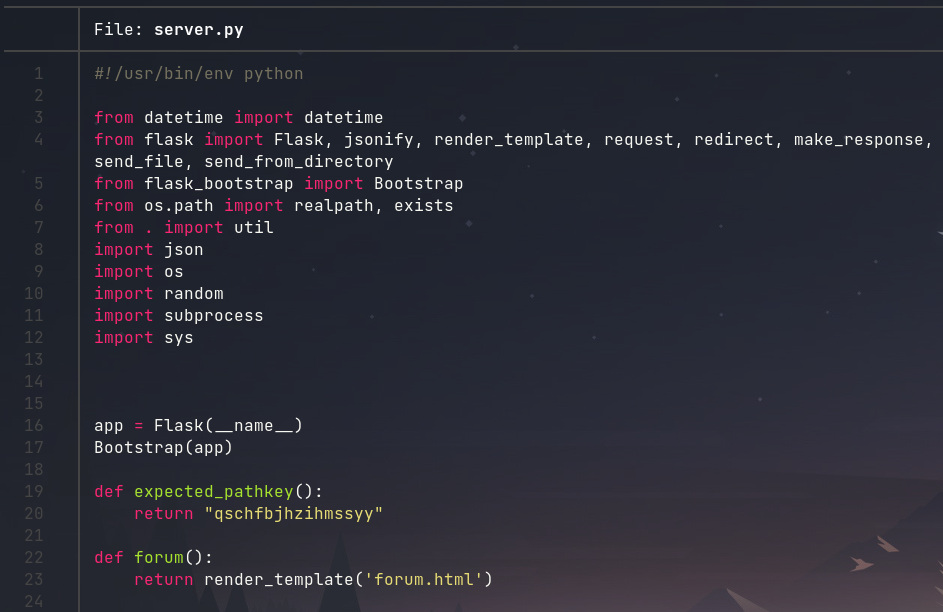
The source code can now be analyzed to determine how to reach the login page for the website. While analyzing the source, it can be seen that this Python Flask web server is using a path key when checking its routes. The path key can be found in the expected_pathkey() function inside of server.py.
Navigating to https://jbjlx<redacted>pcxooy.ransommethis.net/qschfbjhzihmssyy/login reveals the login page. The path key qschfbjhzihmssyy is the solution to the challenge.